1. What is Clickjacking.
It is also known as User Interface redress attack, UI redress attack, UI redressing
It is a malicious technique of tricking a Web user into clicking on something different from what the user perceives they are clicking on, thus potentially revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages. It is a browser security issue that is a vulnerability across a variety of browsers and platforms
2. How to prevent Clickjacking using Filter in java
Below example shows how Clickjacking will happens and how we can prevent the same.
Here I have created a Simple LoginServlet , after successful login, page will be redirected to success page.
Everyone knows how to create servlet and deploy the same. But still I am writing here to understand who have no idea how to create.
Step 1: Start eclipse
Step2: create a Dynamic Web Project ->
Step3: first we need to create a login.jsp page, under Webcontent of the project
<%@ page language="java" contentType="text/html; charset=ISO-8859-1"
pageEncoding="ISO-8859-1"%>
Login page
Step 4: Need to create a success page<%@ page language="java" contentType="text/html; charset=ISO-8859-1"
pageEncoding="ISO-8859-1"%>
Login Success
| Login Successful |
| You can construct page as you like |
Step 5: Now we need to create a LoginServlet
package com.siva;
import java.io.IOException;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
public class LoginServlet extends HttpServlet{
/**
*
*/
private static final long serialVersionUID = 1L;
public void doPost(HttpServletRequest request, HttpServletResponse response)
throws ServletException, IOException {
String username = request.getParameter("username");
String password = request.getParameter("password");
if("siva".equalsIgnoreCase(username)&& "raju".equalsIgnoreCase(password)){
System.out.println("inside if condition");
response.sendRedirect("loginSuccess.jsp");
}
}
}
Step 6: Now we need to do Configuration in web.xml for LoginServletStep 7: Once this configuration done, Now we can run the project using any of the servers like Apache tomcat or Jboss.clickjacking_prevention login.jsp LoginServlet com.siva.LoginServlet LoginServlet /loginServlet
You can use the http://localhost:8080/clickjacking_prevention/
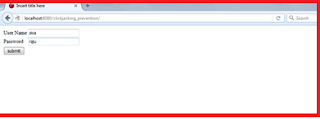
It will open page like above and you can enter username as siva and password as raju, then submit,
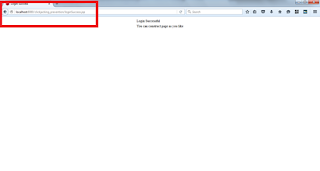
You can redirected to loginSuccess page
Create a html file and provide name as you like and paste the below code.
click jaking
Once we run this html file we can see the same data which is showed in the loginSuccess page
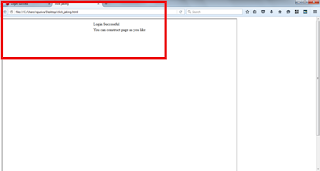
Step 10 : Now we can see the difference between above two images. One is url page and one is iframe constructed page, both are same.
So hacker can use this , and patch in your actual site and steal the data.
Now How to prevent this.
We need to add this code in our filter or jsp page.
response.addHeader("X-FRAME-OPTIONS", “DENY” );
Here I have written Filter to overcome clickjacking
package com.siva;
import java.io.IOException;
import javax.servlet.Filter;
import javax.servlet.FilterChain;
import javax.servlet.FilterConfig;
import javax.servlet.ServletException;
import javax.servlet.ServletRequest;
import javax.servlet.ServletResponse;
import javax.servlet.http.HttpServletResponse;
public class ClickjackingPreventionFilter implements Filter
{
private String mode = "DENY";
// Add X-FRAME-OPTIONS response header to tell any other browsers who not to display this //content in a frame.
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) throws IOException, ServletException {
HttpServletResponse res = (HttpServletResponse)response;
res.addHeader("X-FRAME-OPTIONS", mode );
chain.doFilter(request, response);
}
public void destroy() {
}
public void init(FilterConfig filterConfig) {
String configMode = filterConfig.getInitParameter("mode");
if ( configMode != null ) {
mode = configMode;
}
}
}
Step 11: Once Filter has completed now we need to add same filter configuration in web.xml file
ClickjackPreventionFilterDeny com.siva.ClickjackingPreventionFilter mode DENY ClickjackPreventionFilterDeny /*
Once we have done configuration , you can run the same Iframe example again, you can see the below page without any content, it will show warning in IE and it will not show any details in other browser.
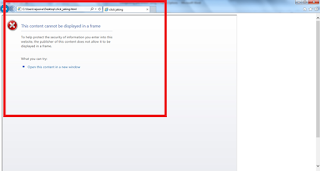
This is how we can prevent the clickjacking attacks.
Thank you for viewing the post.